-
Passphrases
Passwords are something you use almost every day, from accessing your email or banking online to puchasing goods or accessing your smartphone. However, passwords are also one of your weakest points; if someone learns or guesses your password they can access your accounts as you, allowing them to transfer your money, read your emails, or steal your identity. That is why strong passwords are essential to protecting yourself. However, passwords have typically been confusing, hard to remember, an
Download PDF -
Social Engineering
A common misconception most people have about cyber attackers is that they use only highly advanced tools and techniques to hack into people's computers or accounts. This is simply not true. Cyber attackers have learned that often the easiest way to steal your information, hack your accounts, or infect your systems is by simply tricking you into making a mistake. In this newsletter, you will learn how these attacks, called social engineering, work and what you can do to protect yourself.
Download PDF -
Staying Secure on the Road
We want you to be able to make the most of technology at all times, including when you travel. In this newsletter, we cover how you can connect to the internet and use your devices securely on the road.
Download PDF -
Securely Using Mobile Apps
Mobile devices, such as tablets, smartphones, and watches, have become one of the primary technologies we use in both our personal and professional lives. What makes mobile devices so versatile are the millions of apps we can choose from. These apps enable us to be more productive, instantly communicate and share with others, train and educate, or just have fun. However, with the power of all these mobile apps comes risks. Here are some steps you can take to securely use and make the most of
Download PDF -
Securely Disposing of Your Mobile Device
Mobile devices, such as smartphones, smartwatches, and tablets, continue to advance and innovate at an astonishing rate. As a result, some people replace their mobile devices as often as every year. Unfortunately, too many people dispose of their devices with little thought on just how much personal date is on them. In this newsletter we will cover what types of personal information may be on your mobile device and how you can securely wipe it before disposing or returning it. If your mobile
Download PDF -
Using The Cloud Securely
"The Cloud" can mean different things to different people, but usually means using a service provider on the Internet to store and manage your computing sytems and/or data for you. An advantage of the Cloud is that you can easily access and synchronize your data from multiple devices anywhere in the world, and you can also share your information with anyone you want. We call these services "The Cloud" because you often do not know where you data is physically stored. Examples of Cloud computi
Download PDF -
Email Do's and Don'ts
Email is still one of the primary ways we communicate, both in our personal and professional lives. However, we can quite often be our own worst enemy when using email. In this newsletter, we will explain the most common mistakes that people make with email and how you can avoid them in your day-to-day lives.
Download PDF -
Ransomware
Ransomware is a special type of malware that is actively spreading across the internet today, threatening to destroy victim's documents and other files. Malware is software - a computer program - used to perform malicious actions. While ransomware is just one of many different types of malware, it has become very common because it is so profitable for criminals. Once ransomware infects your computer, it encrypts certain files or your entire hard drive. You are then locked out of the whole sy
Download PDF -
What is CEO Fraud?
Cyber criminals are sneaky - they are constantly coming up with new ways to get what they want. One of their most effective methods is to target people like you. While cyber attackers have learned that unaware people are the weakest link in any organization, they have forgotten that knowledgeable people like OUCH! readers can be an organization's best defense.
Download PDF -
Encryption
You may hear people use the term "encryption" and how you should use it to protect yourself and your information. However, encryption can be confusing and you should understand its limitations. In this newsletter, we explain in simple terms what encryption is, how it protects you, and how to implement it properly.
Download PDF -
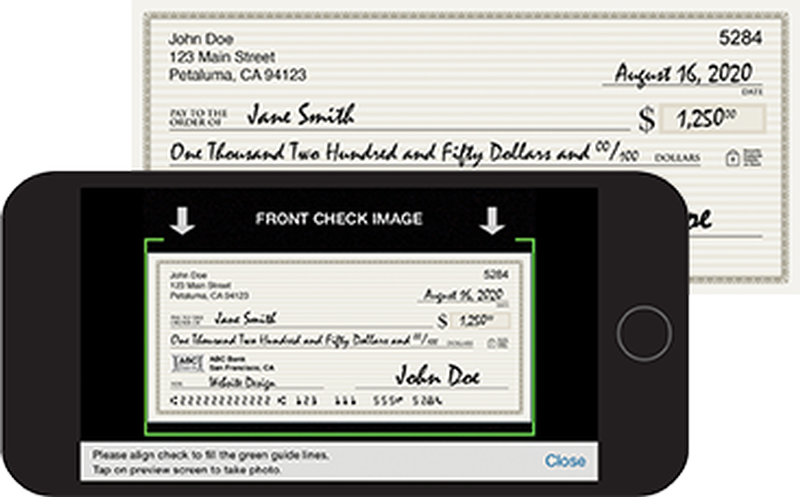
Secure File Transfer
New Market Bank is now offering its customers the ability to send a secure email to the bank. Secure email is a great way to communicate with us and the only way to be sure your confidential information, account number, tax id numbers and financial statements are delivered securely.
Read More -
What is Malware?
You may have heard of terms such as virus, trojan, ransomware, or rootkit when people discuss cyber security. All of these words describe the same thing, types of programs used by criminals to infect computers and devices. A common term used to describe all these different programs is the word malware. In this newsletter, we will explain what malware is, who creates it and why, and most importantly, what you can to do protect yourself against it.
Download PDF -
I'm Hacked, Now What?
We know you care about protecting your computer and mobile devices and take steps to secure them. However, no matter how securely you use technology, you may eventually be hacked or "compromised." In this newsletter, you will learn how to determine if your computer or mobile device has been hacked and, if so, what you can do about it. Ultimately, the quicker you detect something is wrong and the faster you respond, the more likely you can reduce the harm a cyber attacker can cause.
Download PDF -
Internet of Things (IoT)
In the past, technology was relatively simple; you just connected your computer to the Internet and used it for your daily activities. However, technology became more advanced when mobile devices came into our lives, devices such as smartphones and tablets. These devices put the power of desktop computers into our pockets. While far more mobile, these devices also brought their own, unique security challenges. The next big technical advancement is the Internet of Things. The Internet of Thi
Download PDF -
Stepping up for Small Business with PPP Funding
For months now, every facet of “normal” life has been upended by COVID-19. Where and how we work, learn, shop, socialize and even bank have all been affected. Yet, the bright spot amid this sea of change has been America’s enduring spirit as friends and neighbors work together to stay safe, remain connected, and support one another.
Read More
 |
Call Us Today! 952-469-1600 |